How to execute a Privacy Program
This article is the second of a series of articles focused on Privacy. This one covers a proposed approach to structure a privacy program within an organization. The approach suggested is one of many that can be adopted, depending on the nature of the organization. Key components of the program are introduced. These can all be put together in one program or incrementally added depending on scope, time, and budgetary constraints. Several concepts are covered in an overly simplistic form. There are qualified folks out there who can and will contradict the simplistic form… please do it without any hate.
Headers for the Gist
We are all busy. There is so much content out there. The sooner we can get the message, the better. Reading the Headers will give you the gist. Dive in as needed.
Disclaimer
This article is written as a fictional story. Any resemblance to actual events or persons, living or dead, is coincidental. Yet, the concepts discussed, laws mentioned, historical events outside the context of the story, are real. Historical events mentioned are sequenced to support the flow of the story. The goal is to make the subject easy to understand by keeping it light without losing its essence. This article has not been endorsed by any privacy or legal authority (public or otherwise). It is built on our experience of implementing a successful CCPA Compliance Program. The article borrows from several concepts and ideas discussed in other texts on privacy, which have been paraphrased as seen fit.
The program structure discussed would better suit compliance to the California Consumer Privacy Act (CCPA). The EU General Data Protection Regulation (GDPR) and Brazil’s Lei Geral de Proteção de Dados (LGPD) comprise of requirements that have not been covered in the suggested approach. This article is not meant to replace legal counsel within the organization or from outside counsel. Please exercise discretion in using the content… the supermarket approach is suggested… take what you need, leave the rest.
Recap
- In the beginning… Jack sets up a retail store, JStore, that begins to prosper and builds a large base of customers, employs a lot of people, and works with a bunch of vendors and partners
- Marketing, Social Media, Personalization… resulted in customer personal information being captured and exchanged between JStore and its vendors and partners
- So Much Personal Information… from customers, employees, applicants, and vendors / partners was available to JStore
- Data from Everywhere, Stored Everywhere in Every Form… meant that JStore had data in all forms, stored in multiple technologies and in several data sources
- Exchanging Data with Vendors and Partners… increased the Third-Party Risk that JStore was exposed to
- Flawed Data Usage and Storage made Data Protection hard… Information Security became a growing concern at JStore
- Bring on the Data Breaches… With data breaches becoming more common, data protection became a priority for JStore
- Third-Party Contract Management became a crucial activity… to help limit exposure to third-party risk
- Edward Snowden’s revelations put a spotlight on Privacy… making government bodies and companies alike scrutinize their privacy and data protection practices
- Laws were passed with specific privacy requirements… making it important for companies to comply to specific privacy requirements
- Let’s get that Privacy Program Going… JStore embarks on its journey to comply with privacy laws
Setting up Mission Control to lead this mission
JStore kicked off their preparation for privacy compliance by hiring Paul as their Privacy Officer. On Paul’s recommendation, ReCAST was brought on to steer the program. ReCAST put together a program structure that comprised of a Core Team that was responsible for plotting the course for the rest of the privacy program. The members of the core team included:

The program structure established by ReCAST facilitated the execution of a large multi-portfolio initiative. This structure enabled the core team and associated teams (collectively, the program team) to accomplish some key tasks. These tasks included requirements formation and prioritization, decision making, risk identification and mitigation, communication within and outside the program, and finally, supporting development and implementation.
Let’s define the Mission
The core team decided to take the approach of building a Minimum Viable Product (MVP). To this end, they finalized the requirements for the MVP.
The laws to be complied with
With guidance and approval from Lisa, the General Counsel, Clara, and Edith identified the California Consumer Privacy Act (CCPA) as the key law to be addressed. They decided that this law would be at the core of the requirements.
The key requirements for compliance
With guidance and approval from Lisa, the General Counsel, Clara explained that CCPA laid out clear requirements for the rights of the data subject regarding their personal information. Some of the key ones to be addressed were:
Right to Know: provide notice to data subjects at or before the point of collection of personal information

- Right to Access Personal Information: provide a report to the data subject on their personal information captured, processed, stored, and shared by JStore
- Right to Delete Personal Information: delete their personal information from JStore systems and records; inform third-parties and service providers to do the same
- Right to Opt-Out of Sale of Personal Information: refrain from sharing the data subject’s personal information to third-parties who use and share the PI beyond the business purpose stated in their contract
- Right to not be Discriminated against for exercising their Rights: refrain from treating a data subject any differently for exercising their rights under CCPA
- Other requirements around placing a “Do Not Sell My Personal Information” logo on the website home page, providing financial incentives, training requirements, etc.
The regions to be covered
The Privacy Committee determined that United States would be the region covered under the privacy program since JStore did not have any presence in other regions.
The timeframe for compliance
The core team was instructed that JStore needed to be compliant by 01 Jan of the following year. This gave them less than a year to prepare for compliance.
Making sense of the jargon… how about a Glossary of Terms?

Since most of the technology and business teams were not familiar with legal terminology, the core team published a Glossary of Terms that was easily accessible to the program team. This glossary included terms like Customer, Employee, Vendor, Data Subject, Personal Information, Personally Identifiable Information, Third-Party, Sharing, Receiving, Sale (under CCPA), Cookies and Tags, and other relevant terms. Over the program duration, this list grew to also include JStore specific terms and acronyms, application names or business processes and anything the core team felt would reduce ambiguity across teams.
Which Teams are Part of this Mission?
Knowing who to include in the larger program team required a better understanding of the key touchpoints the customers had with JStore. Cal, from ReCAST, worked with the core team to determine all inbound and outbound channels of interactions. This was an interesting exercise that took Cal beyond the core team and into business teams that had not yet been introduced to this privacy initiative. Naturally, they were more than just a bit curious to know what this was all about. Luckily, Cal had done this before and knew what to expect. After due explanation, he gleaned crucial information from them about the processes involving JStore’s customers. Cal finally produced a list that included stores, website (computer and mobile), phone (customer support), emails and texts (customer support, order management and marketing), and direct mail (marketing).
Cal proceeded to determine the touchpoints for employees and vendors. Below is the list of business portfolios that were included in the overall program team:
- Marketing
- Digital Commerce (website and mobile apps)

- Finance (including payment and controllers)
- Procurement
- Human Resources (including Talent Development / Training)
- Stores
- Supply Chain (fulfilment across distribution centers, transportation, factory-ship vendors)
- Merchandising
- Corporate Communications
- Information Security
Organizing the program into tracks
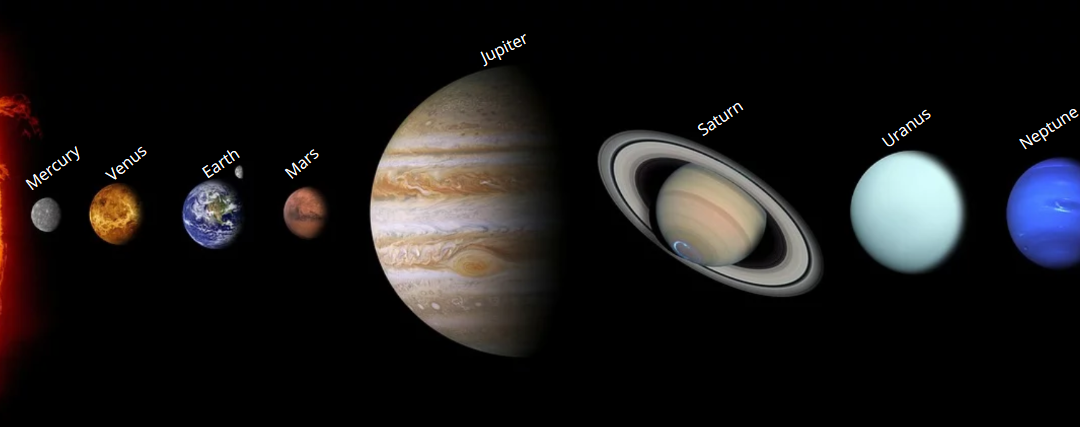
Once the program team was established with clear sight of an MVP, the next step was to decide how the program would be organized. The privacy program tracks, and their interactions with each other, is analogous to our Solar System… with the Sun at its center and 8 planets in orbit.

Data Inventory
The Sun of this solar system. The Data Inventory feeds the entire system. A weak Data Inventory, like a weak Sun, spells disaster for the planets in orbit. A good Data Inventory comprises of three kinds:
- Business Processes Inventory: is a list of all business processes within the organization, including the ones that interact with a data subject’s personal information
- Application Inventory: (aka Asset Inventory or System Inventory) is the list of all technology assets that capture, process or store data
- Vendor Inventory: holds the details of all third-parties or service providers the organization interacts with, including those that exchange personal information with the organization

Privacy Governance

Mercury. The first of the four terrestrial planets. Closest to the Sun with the shortest orbit. The track oversaw the establishment of the Privacy Governance Model. This model governs privacy initiatives and lays down the structure and policies for the organization to follow. Like Mercury’s short orbit, this track was one of the first to be completed in the program.
Notice and Consent
Venus. The hottest planet in the solar system and one of the brightest objects in Earth’s sky besides the Sun and Moon. Providing notice to data subjects at or before the collection of personal information and obtaining appropriate consent are both critical to compliance. As with Venus, notice and consent are highly visible outside the organization and are subject to scrutiny from a legal and user experience viewpoint.

Data Subject Rights

Earth. Third rock from the Sun. The liveliest planet with “intelligent” beings (in short supply!), is also the densest planet (how fitting!). Like Earth, this track dealt with people; lots of them, both within the organization and outside. Data Subject Requests – Access, Delete, Opt-Out of Sale – were all addressed by this track. Dense… on so many levels!
Contract Remediation
Mars. The Red planet and the last of the terrestrial planets. Dealing with the remediation of contracts can be dry work… not unlike the planet itself. The planet is also said to have had intelligent life at some point in its history… ironic, isn’t it? 😉 This was a crucial track that took a lot of work. Updating contracts to include clauses to protect the organization from being exposed to a third-party’s non-compliance meant a lot of back and forth with third-parties… imagine!

Records Management

Jupiter. The first of the gas giants and the largest planet. Managing billions of records of data is no small task. The sheer volume of data being captured these days compares to the planet’s size. The rapid rate of data collection almost matches Jupiter’s rapid rotation – less than 10 hours for it to complete a day. The significance of this track was to ensure the capturing, processing, retention, and destruction of data was done appropriately. More data, more risk.
Data Protection
Saturn. Second gas giant and second largest planet. Like the rings around Saturn, Data Protection has many layers… each layer of protection is an attempt to secure the data from breaches. This track executed Application and Vendor Risk Assessments to identify and plug deficiencies that posed risks to the organization.

Privacy by Design (PbD)

Uranus. This unique planet is tipped on its side… its poles point towards the sun. Privacy by Design is also unique in the sense that, if done right, it embeds all initiatives across the organization. This track ensured privacy practices were incorporated from the initial stages of new technology and business initiatives.
Training and Awareness
Neptune. The planet farthest from the Sun. This is not to say that Training and Awareness was the last on the list of priorities, but it was one of the final aspects of the program. Content for Training and Awareness relied on the completion of certain tracks and hence was initiated mid-way through the program to allow for dependent tracks to attain sufficient clarity and shape. This was a key track that helped inform and educate the organization about privacy as a whole and was key to achieving compliance.

Identifying the right tools for the Mission
Like the tools and equipment used in a space mission, the privacy program also deployed key tools and modules from Privacy Enabled Technology vendors. Some of the tools deployed helped serve important functions:
- Data Assessment to help build the Data Inventory and PbD Assessments
- DSAR module to respond to Data Subject Access, Delete and Opt-Out of Sale Requests
- Website Scans to detect cookies and tags on the website
- Data Source Scans to identify PI in applications (assets)
- Cookie Consent Management to handle cookie consent on the website
- Vendor Risk Management to help with Vendor Risk Assessments and managing vendors
Plotting the course for the journey
“The team is in place, high-level requirements drafted, tracks defined, tools identified… phew! We’re done… can we kick this off now?” Nope, not quite! The missing piece was obviously the timeline. This simple artifact charted the course for us and highlighted key milestones along the way. These mile-markers allowed us to gauge our progress and course correct, as needed.
Many tweaks were made to the timeline through the program – some expected, some totally unexpected, some hurt, others were pleasant surprises. But overall, it was good to have something that served as a gyroscope for our flight through the solar system.
It was finally time to… Blast Off!!