Why Privacy is a Big Deal Now
This article is the first of a series focused on Privacy. This one covers the brief history of why privacy has become such a big deal these days. It is very brief, so please don’t prepare your theses (plural of thesis, you ignoramus!) based on this read. Several concepts are covered in a simplistic form. There are qualified folks out there who can and will contradict the simplistic form… please do it without any hate.
Headers for the Gist
We are all busy. There is so much content out there. The sooner we can get the message, the better. Reading the Headers will give you the gist. Dive in as needed.
Disclaimer
This article is written as a fictional story. Any resemblance to actual events or persons, living or dead, is coincidental. The concepts discussed, laws mentioned, historical events outside the context of the story, however, are real. Historical events mentioned are sequenced to support the flow of the story. The goal is to make the subject easy to understand by keeping it light without losing its essence. This article has not been endorsed by any privacy or legal authority (public or otherwise). It is built on our experience of implementing a successful CCPA Compliance Program. The article borrows from several concepts and ideas discussed in other texts on privacy, which have been paraphrased as seen fit.
In the beginning…
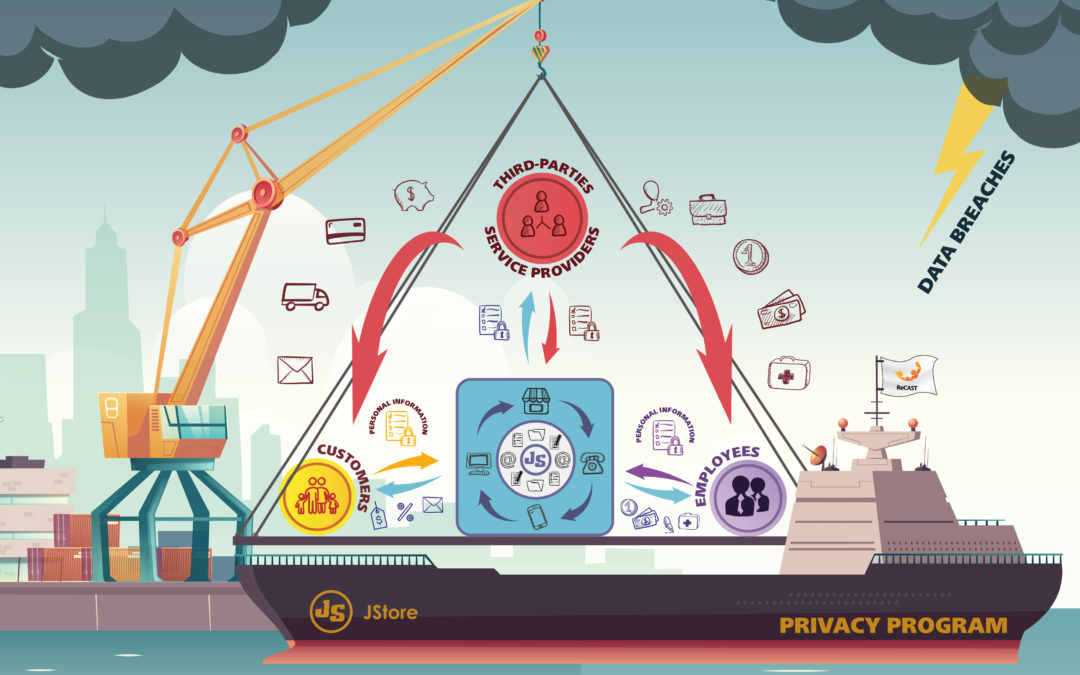
Once upon a time, there lived a man named Jack. Jack opened a department store called JStore. JStore started doing well. Naturally, JStore expanded to several stores across the nation. They had a lot of customers and were getting more by the day.
Eventually, they also started selling their fares on a website. They hired more people and built a large headquarters to office all their employees. Their vendor (Third-Party or Service Provider in legalese) count increased as they added new products, services, and regions. The company supported this growth with IT systems to account for all that data coming through.

Marketing, Social Media, Personalization
In a bid to increase sales, Marta, the Chief Marketing Officer (Marketing department), started sending Direct Mail to customers. Using services offered from Marketing Vendors, she got new customer contacts. Marketing heaven! Email Marketing followed, with promotions, coupons and discounts offered to customers.
Then came Social Media Platforms… all these people looking to congregate online and talk about stuff that is important to them… what they like and dislike, what they do and should do but don’t do and other truly life-changing mumbo-jumbo. Suddenly, there were so many people all in one place that JStore could sell their products to. Perfect! With cookies and tags, Marta was able to promote the right products to individuals… a concept called Personalization (ever wonder how that red dress keeps stalking you from site to site? It’s magic… from a privacy perspective, the dark kind…).
New Marketing vendors came along that connected shopping experiences across other retailers and channels. They compiled all the information about each individual in one place. By subscribing to these vendors, Marta could further target her customers… Targeted Marketing. More heaven!
So Much Personal Information
So much data on customers – their contact information, preferences, shopping and browsing habits, credit information, demographics, purchase history, household information… basically, customers’ Personal Information… they captured it all. They also had a lot of employee data with employment history, social security number, driver’s license, banking information, criminal background, beneficiaries… employees’ Personal Information. They also captured similar information on Applicants who applied to work at JStore (applicants’ Personal Information).

Data from Everywhere, Stored Everywhere in Every Form

Data flowed into JStore through many channels – in stores, online, on the phone, via social media, in chat windows, from vendors, employee applications… several touchpoints. It came in all forms – structured data (databases, fixed form files, etc.) and unstructured data (paper, emails, text files, social media input, media files, etc.). Ian, the Chief Information Officer (Information Technology department), did not want to lose any of the data. He got the company to spend millions of dollars to store it effectively. He even stored the data in the clouds… (what? There are several cloud service providers and most folks use more than one).
They stored it in many systems… a concept called Data Redundancy. These systems are collectively known as Data Sources. Systems were integrated with each other with data going back and forth from the website to the cloud(s) to data centers. To further protect the business during an unforeseen disruption, he stored the data in data centers at different locations… to support, Business Continuity & Disaster Recovery.
Then the idea of analyzing the data to find patterns and trends became trendy (pun intended!). So, Ian & his team built a Data Lake into which they dumped information from several databases (think sewage dumping). This was with the haloed aim of analyzing the data… a discipline called Data Analysis. Now they had all this wonderful data in several places, redundant and all mixed up with each other in a data lake, with no catalog of what was where and why it was wherever it was… and in some cases, how it even got there. But at least they knew it was all over the place. Everyone in the industry and other industries was also doing it… they didn’t question the concept or their implementation of it.


Exchanging Data with Vendors and Partners
Marta was already using Marketing vendors to get more holistic information about her customers. She first had to share her information on customers to get it enriched by the vendors. This resulted in the exchange of customer personal information with vendors.
In the meantime, Hilda, the Chief People Officer (Human Resources department), was also working with vendors. These vendors provided services to handle the employee application process, conduct background checks, provide employee benefits, run payroll, etc… Employee personal information was flowing back and forth with these vendors.
Fiona, the Chief Finance Officer (Finance department), partnered with a local bank to offer JStore branded credit cards to their customers. This meant JStore would send customer information to the bank for processing credit card applications and other transactions on the card. JStore also shared customer information with other partners for services provided to customers.
JStore was sharing personal information with vendors and partners besides storing it themselves. What about the vendors’ vendors (aka Fourth or Fifth Parties)? This then, was the birth of Third-Party Risk, which simply means the risk a company is exposed to by sending data to an entity external to the company and their storage controls and sharing practices.
Flawed Data Usage and Storage made Data Protection hard
In stores and headquarters, employees had paper copies of this information. Some downloaded information from systems and sent them over emails; some stored it on their personal computers or on shared drives. Some were careful with it, most were not. This gave Sara, the Chief Information Security Officer (Information Security department), ulcers. She could never be sure how data was being used or stored and whether it was secure across the company. With the sharing of data with vendors to add to her misery, Sara built processes to assess the risk to data safety across applications and vendors – Application Risk Assessment and Third-Party Risk Assessment, respectively.


Bring on the Data Breaches
As this capture of data became standard across industries, word spread. Some smart people with not very noble intentions hacked into these company websites, databases and networks and stole the information for nefarious activities. Data Breaches came to the fore in 2004 with the AOL breach, in which 92 million email addresses were sold and used for spam. Such breaches sprouted across the globe impacting companies, large and small.
Then came the prominent breaches at Yahoo, eBay, LinkedIn, and Equifax. A lot of personal information was getting leaked. People were getting furious because their information was now in untrustworthy hands.
This meant more ulcers for Sara. She now had to build a process to respond to a data breach – the Data Breach Response Plan or a privacy subset, Privacy Incident Response Plan. It included a plan to inform the right people with the right data within specific time frames and engage the right team to remedy the situation.
Third-Party Contract Management became a crucial activity
Pete, the Chief Procurement Officer (Procurement department), was getting busier by the day with the onset of more vendors and/or partners (third-parties or service providers). He worked with Lisa, the General Counsel (Legal department), and her team to ensure the contracts for these third-parties had all the necessary terms and conditions to protect JStore from exposure to data breaches of the third-party’s systems. Sara provided her approval only if she was satisfied with the results of the Third-Party Risk Assessment.

Edward Snowden’s revelations put a spotlight on Privacy

In June 2013, Edward Snowden leaked secret documents about how the US National Security Agency (NSA) spied on Americans and people across the globe. This revelation created quite a storm for obvious reasons. It resulted in companies tightening their privacy & security controls. Governments became protective of their citizens’ privacy. There was scrutiny on the transfer of data across international borders, on the security of data while being transmitted (data in transit) and stored (data at rest), who had access to this data (access control lists or ACLs), etc.
Laws were passed with specific privacy requirements
The US Privacy Act of 1974 was the first privacy-specific law passed in the United States. Industry-specific laws followed – Health Insurance Portability and Accountability Act (HIPAA) in 1996 that targeted the Healthcare industry and Gramm-Leach-Bliley Act (GLBA) in 1999 for the Banking and Financial industry. Children’s Online Privacy Protection Act (COPPA), passed in 1998, took a first step at regulating personal information collected from minors via websites. Other nations also passed privacy specific laws, with the European Union’s General Data Protection Regulation (GDPR) of 2016 being the first foundational law that defined clear privacy requirements for companies operating in the EU to follow. The California Consumer Privacy Act (CCPA), passed in 2018, enhanced the privacy rights for residents of California, United States.
Among other aspects, the requirements defined personal information of an individual (data subject) and addressed when to provide privacy notices, details on capturing consent to data processing, the right to request a copy of personal information or to delete this information. Other laws are already in the making across the United States and globally.
In addition to privacy, laws were passed that articulated the requirements for breach notifications in the event of a data breach. Data Retention laws and regulations were also passed to provide expectations on how long data should be stored in a company.
Let’s get that Privacy Program Going
Lisa insisted that they needed to act now to avoid any legal consequences. Sara agreed, since data protection was getting extremely hard and the risk of a breach was growing by the day. Fiona wanted to avoid any major financial obligations that would come with a data breach or non-compliance to laws. Rita, the Chief Investor Relations Officer (Investor Relations department), knew the company could ill-afford any negative publicity given the recent drop in its stock price. This worried Jack.
Marta and Hilda were concerned this might result in reduced leverage of vendors, which could limit their capability. Ian worried about the work coming his way to fulfill the compliance requirements and secure systems against breaches. Pete knew he had his work cut out with all the communication that would be needed with vendors and partners.

Jack approved the creation of a Privacy Program. They formed a Privacy Committee that comprised of all the key stakeholders – Lisa from Legal, Sara from Information Security, Fiona from Finance, Marta from Marketing, Hilda from Human Resources, Ian from Information Technology, and Pete from Procurement. Jack assured them of his support and told them to pull him in when needed.
Given their lack of experience in this space, they decided to hire a Privacy Manager to help identify next steps. After an extensive search, they hired Paul as their Privacy Officer and the first member of the Privacy Office.
Paul also became a member of the Privacy Committee. He understood the magnitude of the program and the need for the right expertise. With thorough due diligence, he strongly recommended hiring ReCAST to steer this program. ReCAST specialized in running such privacy programs, had a stellar success record, and had significant experience in the retail industry, making them ideal candidates to help JStore in this venture.
What followed was a unique, arduous, frustrating, but eventually successful journey towards compliance.